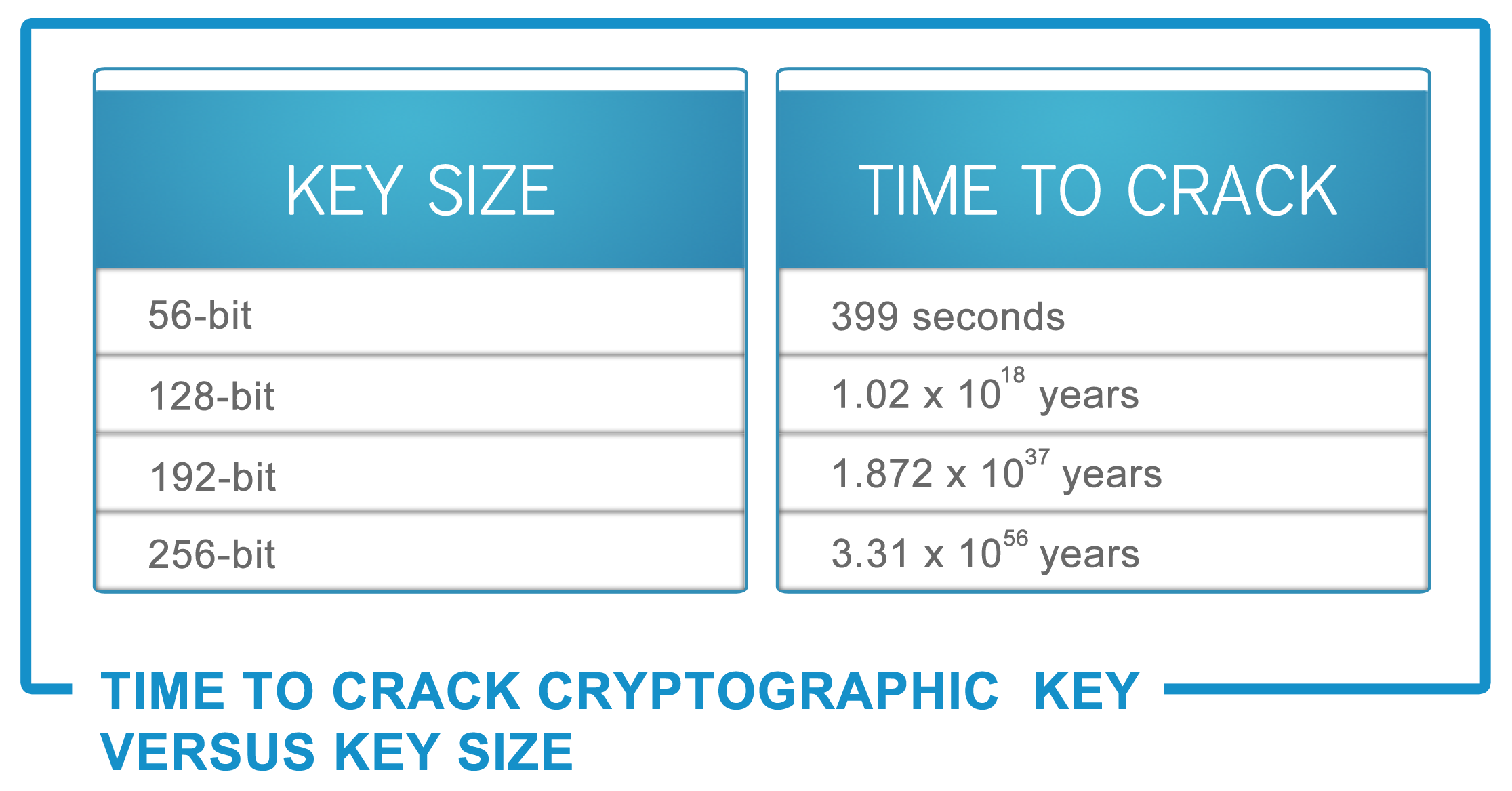
So, what is your mental image of data? A large Excel spreadsheet; lots of ones and zeros like in the movie 'The Matrix'; or how about a large cork notice board with lists of all your customer information pinned to it. Regardless of how you see it, you need to ensure that 'others' don't.
We’ve covered email document encryption, as well as password protection in our email security blog series so far. I’m taking a step back to the 'notice board' and addressing the complex issue of data security.
There are those that will always devise methods to gain access to your notice board. To combat and mitigate the risks of a data breach, various techniques can be implemented, as discussed in a previous blog post: What do they do with my data?
If you have a huge notice board and the ability to sort and segregate your customer data into sections to target them for specific products/offers, then you have Big Data. The risks associated with that have also been discussed in a recent post: Leveraging Big Data to deliver the one-to-one message? Don't get caught in a trapThe measures you have taken to stop people seeing, or accessing the notice board, constitute your data security, but do you have peace of mind?
For the sake of ‘sleep-easiness’, it is best to check-in with the compliance and regulatory guys. There are two primary areas of legislation that have been devised to protect two of the most sensitive types of customer information - although they may not necessarily apply to every industry. They are health records and credit card details. Get more details here.
By making use of the “reasonable safeguards” you will have peace of mind that your notice board is protected. But, what safeguards will you take to maintain the protection of your customer data once it has been copied into your eDocuments from your uber-secure notice board?
For example, you are going to send each of your customers their statement/invoice/policy document/payslip etc. from every line across your notice board. For the electronic format, you or your ESP will create a document and email it to your customers. You need to maintain a high level of security throughout the process.
On the actual email cover page – the bare minimum:
Data security need not be the 'big monster'. Some industry best practices along logical representation of data and behind the correct levels of authentication will do the trick.
Do you need further advice on how to safeguard your customer data when sending eDocuments? Contact an eBilling expert here.
How do we protect the notice board from prying eyes, and those bent on evil?
There are those that will always devise methods to gain access to your notice board. To combat and mitigate the risks of a data breach, various techniques can be implemented, as discussed in a previous blog post: What do they do with my data?
If you have a huge notice board and the ability to sort and segregate your customer data into sections to target them for specific products/offers, then you have Big Data. The risks associated with that have also been discussed in a recent post: Leveraging Big Data to deliver the one-to-one message? Don't get caught in a trapThe measures you have taken to stop people seeing, or accessing the notice board, constitute your data security, but do you have peace of mind?
For the sake of ‘sleep-easiness’, it is best to check-in with the compliance and regulatory guys. There are two primary areas of legislation that have been devised to protect two of the most sensitive types of customer information - although they may not necessarily apply to every industry. They are health records and credit card details. Get more details here.
- HIPAA (Health Insurance Portability and Accountability Act – USA)
Mandates and regulates the use of electronic processing of personal healthcare information. The crux of the legislation is that companies must ensure reasonable safeguards for patient information, and gain consent from the patient to send to a validated email address. - PCI DSS (Payment Card Industry Data Security Standard – Global)
A set of standards to ensure that all and any companies who store, process and transmit cardholder data maintain a secure environment. Cardholder data specifically must be encrypted at all stages of transmission.
By making use of the “reasonable safeguards” you will have peace of mind that your notice board is protected. But, what safeguards will you take to maintain the protection of your customer data once it has been copied into your eDocuments from your uber-secure notice board?
For example, you are going to send each of your customers their statement/invoice/policy document/payslip etc. from every line across your notice board. For the electronic format, you or your ESP will create a document and email it to your customers. You need to maintain a high level of security throughout the process.
Recommended checklist:
On the actual email cover page – the bare minimum:
- Customer name: This is necessary because personalisation helps assure customers that you are a sender they have previously engaged with and so, they know and trust you.
- Email address: Use the email address your customer provided you with when they gave consent for your communications.
- Display partial account / personal data such as a few digits of social security/ID number: This gives further authentication and verification. It assures the customer that the sender is a valid biller/marketer with whom they have an existing relationship.
- Encryption: All sensitive documents should be distributed in an encrypted format. (I refer back to the first post in the security blog series). All sensitive customer information will then be held in this format.
- Authentication: All eDocuments should be password protected. (Again, refer to the first post in this security series). All these documents should have at least one authentication level; ie. one password/shared secret.
- Confidential data like credit card numbers / social security and ID numbers. These numbers can be hashed out too, with just the last four digits visible. This adds another layer of protection and gives a comfort level to the customer about their private details.
- Additional data, like transaction data or itemised billing can be embedded into the PDF and then encrypted and password protected. It can also be accessed offline.
- Verified online access: Some companies compliment their eDocuments with information held on their online portals. Customers can access the portal from a secure link in the attachment - online access should require further authentication.
- Other data can be hosted online out of the portal. This would also be accessed by user authentication - only from within the attachment and hosted using a randomly assigned GUID.
Data security need not be the 'big monster'. Some industry best practices along logical representation of data and behind the correct levels of authentication will do the trick.
Do you need further advice on how to safeguard your customer data when sending eDocuments? Contact an eBilling expert here.
Simon Johnston
striata.com