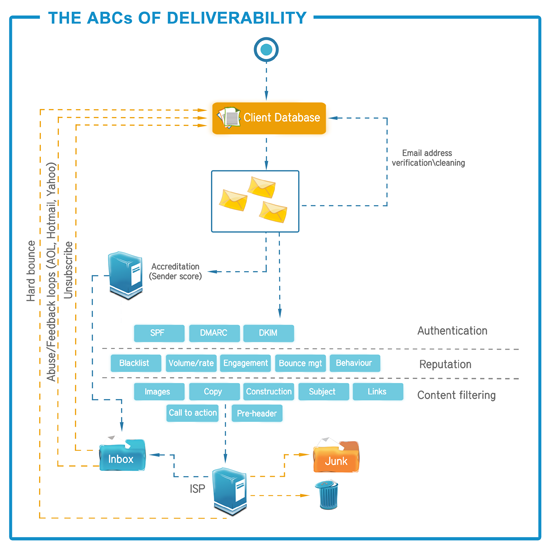
One of the biggest concerns when sending out an email, is whether or not it will be marked as spam by any of the filters it passes through on its way to your customer’s inbox. Even when adhering to authentication standards such as SPF & DKIM, using "warm" IP addresses and ensuring that your email lists are clean; the spam filters have the last say on your deliverability and their decision-making logic is a well kept secret.
There are no well documented algorithms, keywords or methods used to filter emails. What makes the challenge even harder, is that spam filters constantly change their rules to keep up with new methods used by unscrupulous spammers.
Just as illegitimate mass emailers learn the rules to stay one step ahead of the filter software, so too do spam filter rules change and we have to understand the parameters which cause some emails to be cast away.
Don’t get labelled as spam: structure your email correctly
If your email "looks" like spam, it’s likely to be marked as spam by the receiver. You may also find that your campaign starts off with a good deliverability rate, but this quickly deteriorates as the filters "learn" from their users. So how do you structure your email?
The underlying HTML needs to be impeccable. There are rules that must be adhered to when building an email and simply converting a word document to HTML format will not conform to the strict standards.
- Make sure you remove misunderstood "spammy" words and avoid using excessive punctuation or CAPS.
- Identify yourself in the FROM
- Make sure your subject accurately describes the content.
- Have the correct balance of images and test. You’ll want to send it as a Multi-part MIME email (HTML & Text versions).
- Make your email short and sweet so that it is easy to read. You don’t want it being mistaken for spam just because at a glance you could not tell.
- Make sure you have an unsubscribe link so people don’t click the spam button instead.
- Unfortunately, following the above ‘rules of thumb’ will still not guarantee that an email will go straight to the inbox.
The solution is to test, test, test
Start with your content - test your email copy using the many free tools available, then test the entire email as a package by monitoring inbox open rates and previewing emails in multiple email clients. This is essential to an ongoing, successful email send.Adjust and take action
Many of the top ISPs provide a mechanism to report back to the sender whenever a mail is reported as “spam” or “junk” by the customer. Called Feedback Loops, a standardized report is returned as an email which provides the sender with the information needed to remove the email address from the list.ISPs provide a subscription method via a web form, usually on the same postmaster site that is used to register for whitelisting. By entering into the agreement that the sender will monitor and take action on complained email addresses, the reputation is increased and the emails being sent are legitimized.
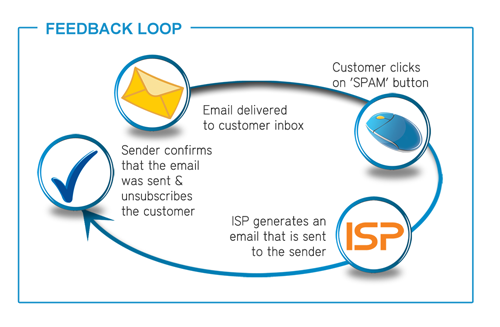
In summary:
- Create a well structured email
- Check the content
- Test before you send
- Adjust if you are getting complaints or see the open rates dropping
We hope you are enjoying our email deliverability series. If you haven’t yet downloaded the white paper, why don’t you do so now? It’s full of easy to understand advice on how to improve deliverability of your emails. Plus it’s free!
Keep following the series, next week I will be covering the big topic of how you get your customers to OPEN your email!
Alex Papadopulos
striata.com