Throughout this series I have
shared tips and tools you can use to help enhance your email
deliverability. In this final instalment, I would like to take you on a
journey 'behind-the-scenes' and discuss some of the technical set-up
associated with deliverability.
When it comes to sending bills
or marketing via email, they are rarely sent from the same domain/server
where the 'FROM' and 'reply-to' addresses exist.
Consider the
common scenario where company X utilizes the services of an email
service provider (ESP). The IP address of the server that attempts to
deliver the emails is owned and operated by the ESP, with no
administrative link back to the company whose emails are being sent to
outside mail exchangers.
To use an analogy, the company is
using a third party courier to deliver its correspondence and it may be
an unknown entity to the recipient. It is therefore necessary to use
technology to prove that the courier has permission to send the package.
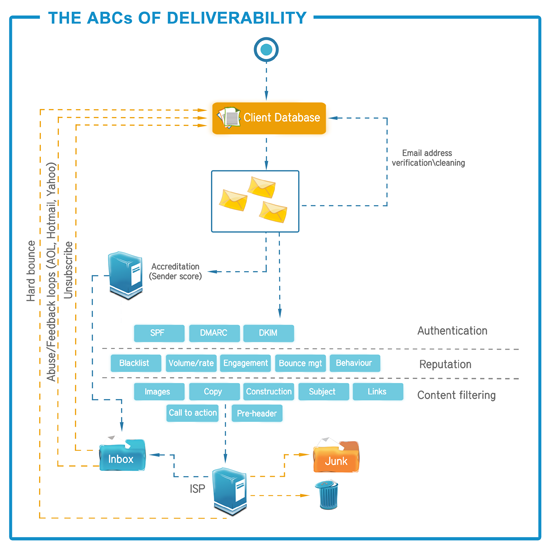
In the world of email, there are two accepted methods of proving that this relationship exists: SPF and DKIM.
 |
Sender Policy Framework (SPF)
|
SMTP, the protocol for email, was designed so that any computer can
send an email to any other computer on the Internet. While this created
an open, easy-to-use system, it also relies on the sender to be honest
enough not to send a mail claiming to be from somewhere else.
As we know this is not the case and spam is almost always sent from one party pretending (or spoofing) to be someone else.
SPF was designed as an anti-forgery system and provides a way for a
receiving email server to verify that the sending mail server has
permission to send the email.
When selecting an ESP, it is very
likely that they will send emails from their servers using your FROM
address. It is for this reason that you MUST give the ESP permission to
send emails using your FROM address (and domain name).
This is
achieved by a simple DNS entry on your domain which lists the approved
senders of your emails, including your internal mail servers.
While SPF deals with the permission to send emails from an ESP on behalf
of a domain, there is a second level of authentication that deals with
the ownership of the actual email message.
 |
DomainKeys Identified Mail (DKIM)
|
A common problem with nefarious email senders is that details of
emails, such as the FROM address and entire contents of emails are often
forged so that they appear to be generated and sent from a legitimate
source.
DKIM controls this problem by making use of
sophisticated cryptographic techniques in order to create a unique
signature for every sent email.
In the courier analogy above,
this is the same as the physical package being stamped with a keyword
that only the actual sender could have possibly known, verifying that
they are the actual sender and not a third party.
While DKIM
signs the email going out; a DNS entry must be made on the FROM address
domain in order to allow the receiving mail server to verify that the
signature has been created from a trusted source. An ESP will assist
with generating keys, as well as the required DNS entry.
The
two methods described cater for the delivery of the message, but do not
provide information on who is TRYING to spoof emails, nor do they allow a
directive to the receiving mail server on what to do if they encounter
spoofed or forged messages.
 |
Domain-based Message Authentication, Reporting & Conformance (DMARC)
|
Allows the domain owner the ability to be notified when forged
messages are being sent to ISPs. This identifies campaigns in the email
environment that are acting against the reputation and best interests of
the company. Reporting is available in simple formats which can be
evaluated in the case of spoofed or forged emails being sent out.
In addition to reporting, DMARC also allows the domain owner to
instruct the ISPs on how to deal with a message that has been forged.
This may be as liberal as allowing the messages into the inbox, or in
the case of companies who are targeted in spam and phishing campaigns to
instruct the ISP to delete any emails that do not have a valid DKIM
signature.
In our example, SPF and DKIM acting as the
mechanisms to authenticate emails equate to the security practices that
can be used in the real world, such as ID badges to help prove
association and stamps or barcodes to prove authenticity.
DMARC
is the last link to the chain and can be compared with a receptionist
who is responsible for receiving and distributing all incoming packages.
By having a prior knowledge and relationship with the senders of
packages and a list of defined rules on what to do when packages are not
delivered from a courier with a suitable ID. This also includes
packages that don’t have the correct packing slip - this person could
take action depending on the circumstance.
Thanks for joining
me on this exciting journey of email deliverability. I hope that you
have found the deliverability blog series interesting and useful!
If you haven’t had a chance to download our new deliverability white
paper '7 steps to better email deliverability', then you can do so now,
simply
click here.
Alex Papadopulos
striata.com






 Lifecycle
communications (such as birthday messages) that are personalized and
triggered on a special date or event are an important component in
engaging customers and increasing loyalty to your brand.
Lifecycle
communications (such as birthday messages) that are personalized and
triggered on a special date or event are an important component in
engaging customers and increasing loyalty to your brand. 

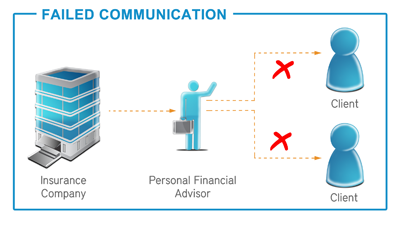
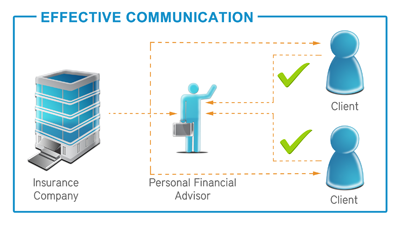
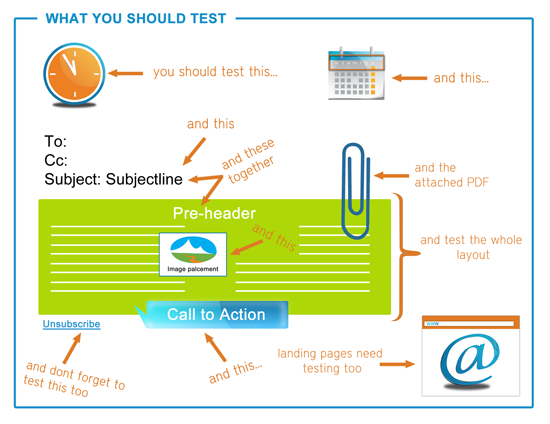
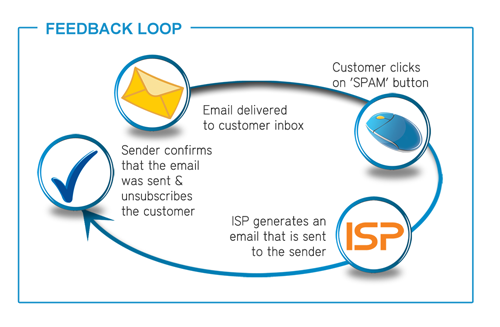
 Taking these steps will minimize the risk of your company and customers
becoming the victims of phishing attacks. If you’d like to find out
more,
Taking these steps will minimize the risk of your company and customers
becoming the victims of phishing attacks. If you’d like to find out
more,